What is a Web Application Firewall (WAF) and Why Do You Need One?
Add a critical layer of security to your network by protecting applications from attack.
Did you know that over two-thirds of web applications have critical security flaws? That is what Veracode found when it scanned 130,000 applications for vulnerabilities, finding some 68% had a flaw that fell into the OWASP (Open Web Application Security Project) Top 10.
OWASP produces an annual list of the top 10 exploits being seen in the wild.
Web applications are a major target for cybercriminals who explicitly exploit known vulnerabilities. Not all these flaws have fixes available immediately, and not all fixes are implemented by IT anyway, leaving these applications sitting ducks.
It doesn’t have to be that way. A Web Application Firewall, or WAF, can block hackers from your applications the same way a perimeter firewall blocks network intrusion. So, what is a Web Application Firewall? On the surface it seems a bit self-explanatory, but the devil is in the WAF details.
We’ll look at these details, show how a Web Application Firewall blocks attacks and demonstrate how to get started.
Why Hackers Attack
The fundamental challenge that IT faces is that web applications have vulnerabilities which are not limited to home-grown applications—we regularly see reporting of vulnerabilities in market leading applications. As we can see from industry analysis, the number of apps with vulnerabilities is significant and nobody can be complacent about how secure their application is.
You may ask, why would hackers attack me? I’m not a mega-corp, I don’t hold state secrets—I don’t have anything of value for them.
It’s more complex than that. You see, hackers are often bent on extraction—more simply put, at the stealing of data. Of course, items like credit card details are obviously of value, but hackers also see value in stealing information such as lists of usernames, as this can be used to craft other attacks.
Extortion via ransomware or threats to publish sensitive information is a key motivator. Again, the size or type of the organization is not necessarily significant to make these attempts worthwhile.
Meanwhile, vectoring is where your compromised web application is used to deliver malware to visiting clients. While no actual damage is done to your application on the surface, there is the potential for reputational damage and having your website blocked by search engines and client protection software.
What is a Web Application Firewall (WAF)?
So, what is a web application firewall? The folks that make the Progress LoadMaster load balancing solution know the answer—because we have one!
“A Web Application Firewall (WAF) builds on and enhances traditional firewall security protection. Traditional firewalls don't stop encrypted HTTPS traffic as they have no visibility of the content within. A Web Application Firewall, which is logically placed between standard firewalls and web servers, operates at Layer 7 of the network stack. It can decrypt HTTPS traffic and inspect the data content. In conjunction with lists of known attack methods, the Web Application Firewall can deny access to web servers when malicious activity is detected,” the Progress/Kemp glossary explained.
Not Your Father’s Firewall
In fact, a web application firewall enhances and complements traditional firewalls which have no visibility into the content of encrypted HTTPS traffic and therefore can’t block dangerous HTTPs streams.
In contrast to traditional firewalls, WAF operates at Layer 7 of the network stack between standard firewalls and web servers, decrypting HTTPS traffic and inspecting the data within. With anomaly detection and lists of attack methods, the web application firewall can block access to web servers when malicious activity is spotted.
The Role of WAF
Let’s look at the topology of a WAF solution. Protecting against vulnerabilities is a multi-layer challenge and one of the most significant layers is the Web Application Firewall or WAF.
So, how does a WAF help? A WAF is a proxy that sits between users and a web application and inspects all traffic for malicious attempts to exploit vulnerabilities, and can block such attempts from getting to the web application.
As part of a layered security approach, a WAF can deliver logging and event information to external security and monitoring services. The WAF uses a set of rules that provide protection against a wide range of attacks—this set of rules has evolved over the years to provide coverage for new and emerging threats. In the case of the WAF available with Progress/Kemp LoadMaster, these rules are updated automatically on a regular basis.
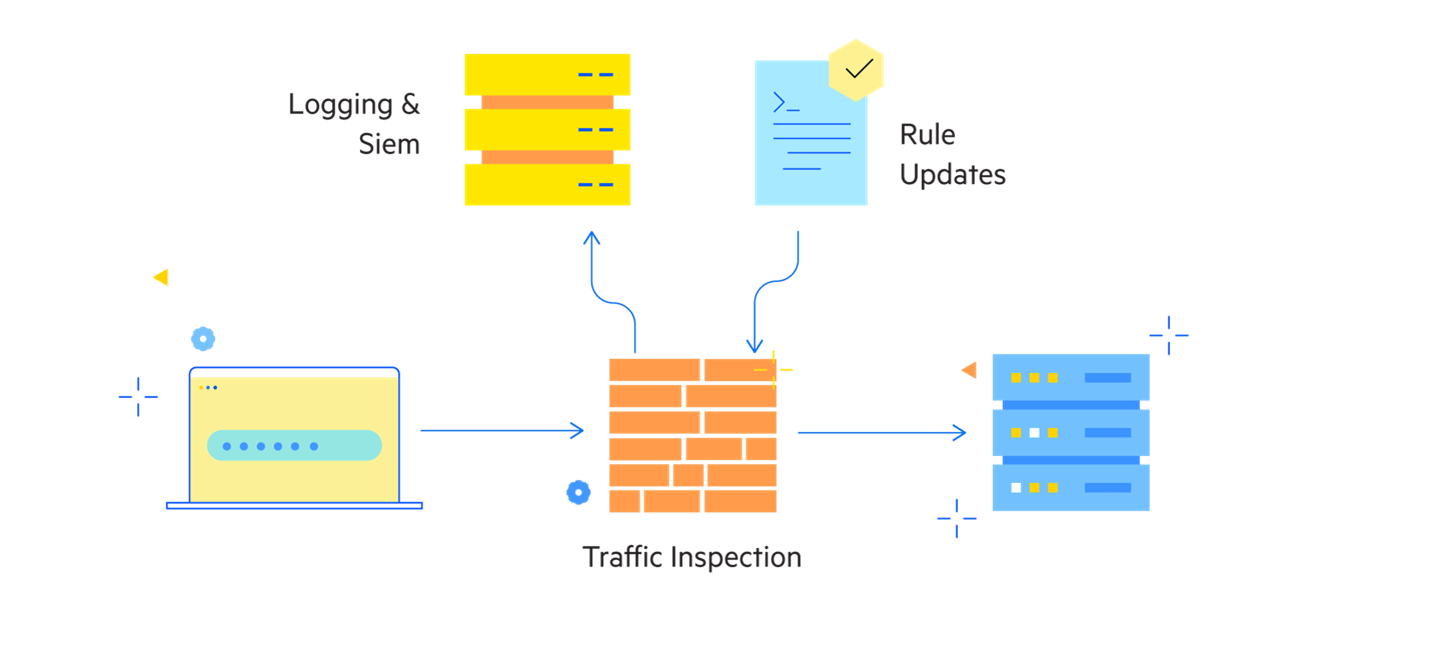
Using the LoadMaster WAF as an example, this WAF’s rules provide protection against the major vulnerabilities identified in the OWASP Top 10.
OWASP are an independent, industry supported group who focus on application security and annually conduct research into application security. Over the years, the vulnerabilities in the OWASP Top 10 have changed as new exploits become more common and older exploits have been mitigated over the years as application vendors fix vulnerabilities. The rules provided by LoadMaster include these older vulnerabilities, alongside application specific protection.
Let’s take a quick look at some of these vulnerabilities and how they are exploited, starting with SQL Injection.
Example of SQL Injection
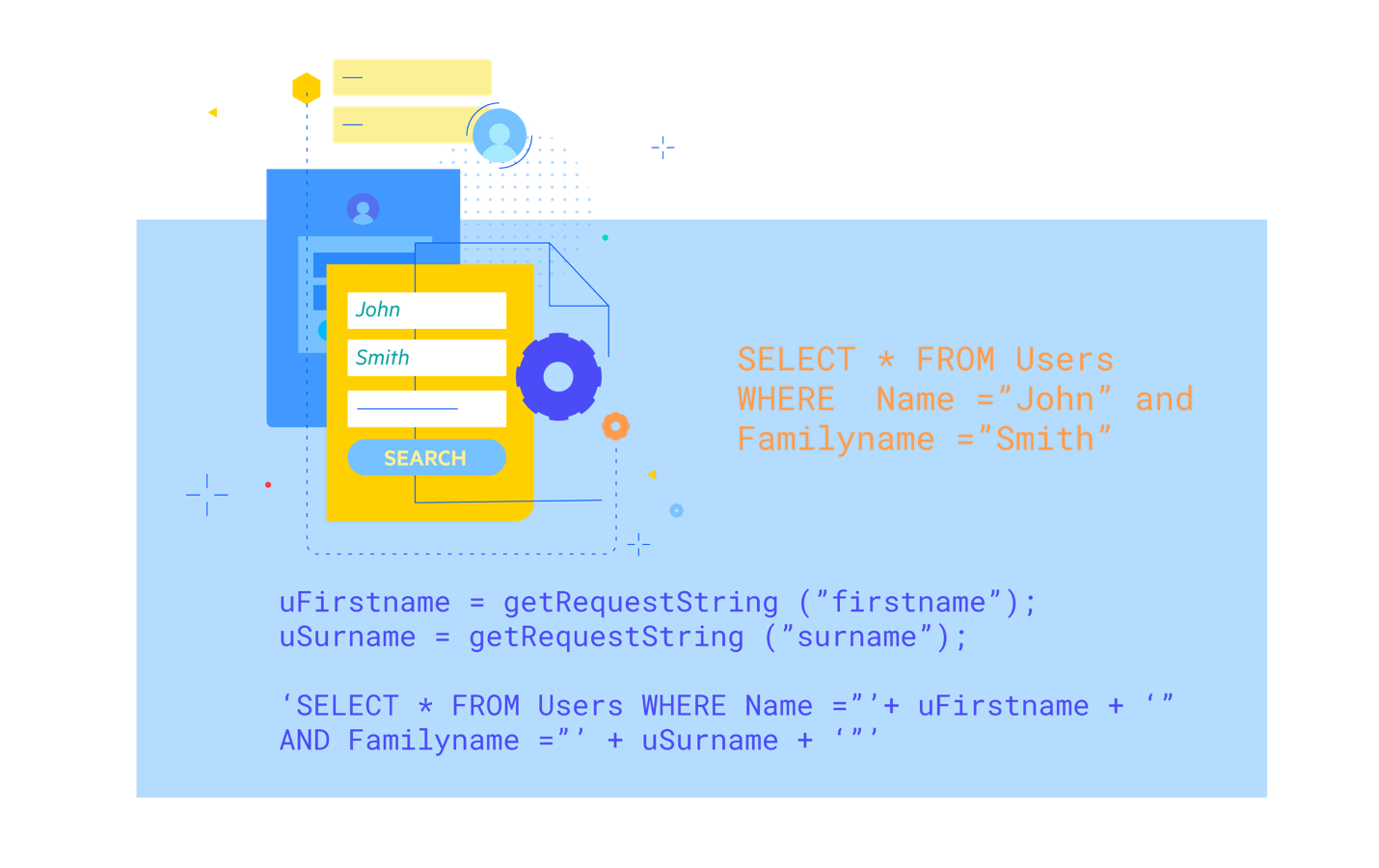
The above illustration shows what an SQL injection attack looks like. An SQL injection attack attempts to modify the behavior of an SQL statement at the back-end server by injecting additional SQL commands.
Here we have a form that takes in variables and an SQL statement is constructed based on the values in the form fields. However, if a malicious actor injects some additional SQL via the surname field, the results returned are completely different.
As 1 = 1 is always true, the statement with a family name will return true. As a result, the SQL statement is actually selecting all users with the first name John—not what was originally intended by the developer.
This simplistic example shows how a web application may be exploited to deliver more data than was intended. Variants of this attack could actually execute SQL drop statements to delete parts of the database.
Example of Broken Access Control
Now, let’s peek at Broken Access Control exploits. With broken access control, a user can act on resources outside their intended permissions.
In the below example, we see a normal access where a user accesses their own account. However, if they modify the parameter on the HTTP request, they are allowed to access someone else’s account. Again, not exactly a desirable outcome.
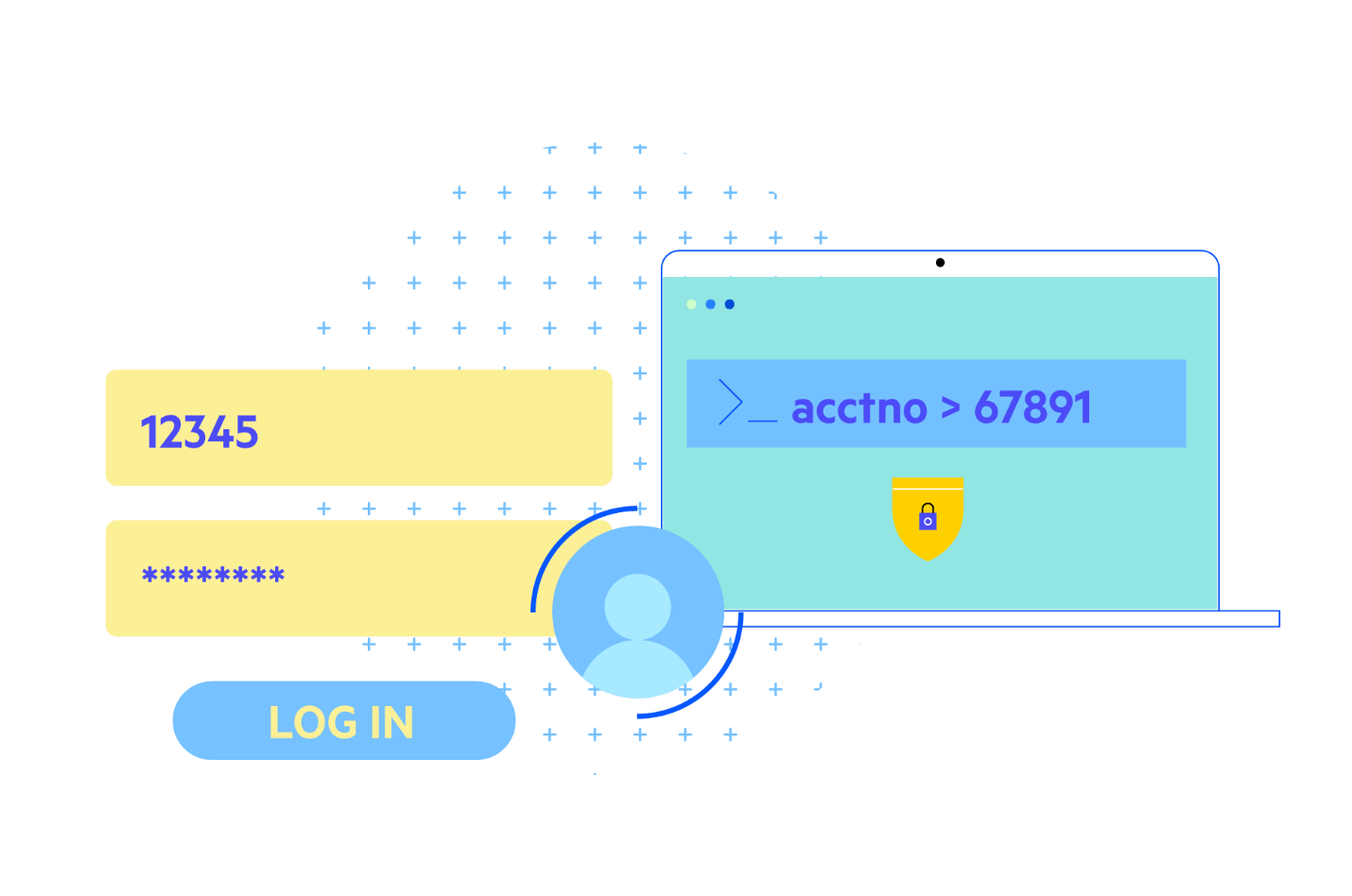
These two are very simplistic—applications should be coded much better than this—but they may still be susceptible to well-crafted attacks designed to exploit a very specific weakness.
Application weaknesses may be inherited from third-party or open-source components which when updated may introduce new vulnerabilities. This is why application protection should be ongoing and not just based on periodical security checks such as app penetration tests.
Inside the LoadMaster WAF
The Kemp WAF offers in-depth defense for web servers, applications and your website, protecting both custom and off-the-shelf applications from vulnerabilities such as SQL injection and cross-site scripting (XSS).
With Kemp WAF, IT can create security profiles for each application and comes equipped pre-integrated rulesets for common attack vectors, stopping specific traffic patterns indicative of malfeasance from reaching your applications—without modifying your applications or infrastructure.
Protection Against OWASP Top 10 Attacks
As mentioned earlier, the Open Web Application Security Project (OWASP) Top 10 identifies the most common and critical web application attacks. LoadMaster WAF has pre-defined rulesets to fight these very vulnerabilities. Built-in WAF protections include:
- Cookie Tampering
- Injection Attacks
- Cross-Site Scripting (XSS)
- Data Loss Prevention (DLP)
- Buffer Overflow Protection
- Access Control
- Security Misconfiguration
- Real-Time Protection
- Denial of Service Protection
- Botnet Attack Preventions
- Web-Based Malware Protection
- Zero-Day Threats
Listen and Learn
Learn more about web application firewalls, and get the skinny on setting up a WAF by tuning into our Web Application Firewall 101: What is WAF? webinar.

Maurice McMullin
Maurice McMullin was a Principal Product Marketing Manager at Progress Kemp.
