Enterprise Data Security Guide for Big Data, Cloud & Relational Databases

Securing your data has never been more important, but enterprise security has also never been more complex. Join us for a webinar to explore your options.
Enterprise data security is one of the foremost topics in data access today and, unfortunately, it’s also one of the most complicated topics. Cyber attacks are relentless and are not going away. The collective costs of data breaches are painfully high. None of us want our company to suffer these losses or make the headlines because of a security breach.
Data security is complicated for a variety of reasons. You have security threats, users misusing their credentials, compliance standards and laws to understand and satisfy. And finally, you must evaluate an unending list of technologies and solutions to meet your product’s environment and architectural security needs.
Data Security Landscape
There are a substantial number of distributed technologies required for a robust security implementation, as seen in the graphic below. You must identify that the client is who or what they claim to be, noted in green. You must determine what data and actions are accessible to the client, noted in blue. You must secure the data as it moves by means of encryption, noted in purple. And you must monitor and/or trace access and movement as it occurs, noted in orange.
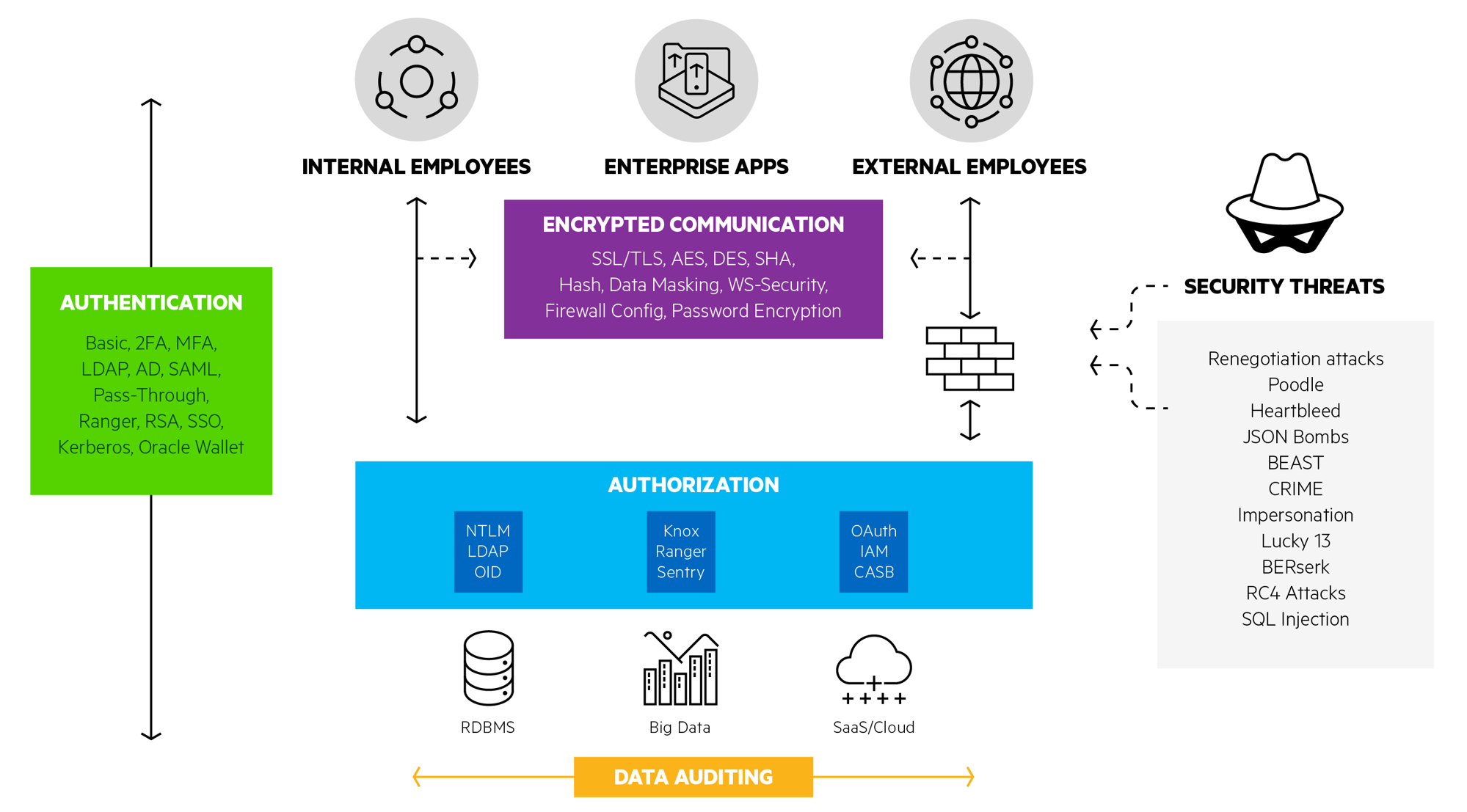
In our recent webinar, Enterprise Security in Data Access, we took a deep dive into each of these topics:
- Authentication: How do you ensure that an individual is who/what they claim to be?
- Authorization: How do you determine what actions an individual can or cannot perform?
- Encryption: How do you protect data at all times, at rest, in motion, or in use?
- Data Auditing: How do you asses the quality, utility and security of data as it moves between systems?
In addition, we also discuss network security options such as CASB, or Cloud Access Security Brokers, and topics specific to securing big data and cloud implementations, such as Amazon AWS’s IAM, or Identity and Access Management.
During our webinar, we polled the hundreds of attendees to learn where companies are seeing increasing complexity with data access security.
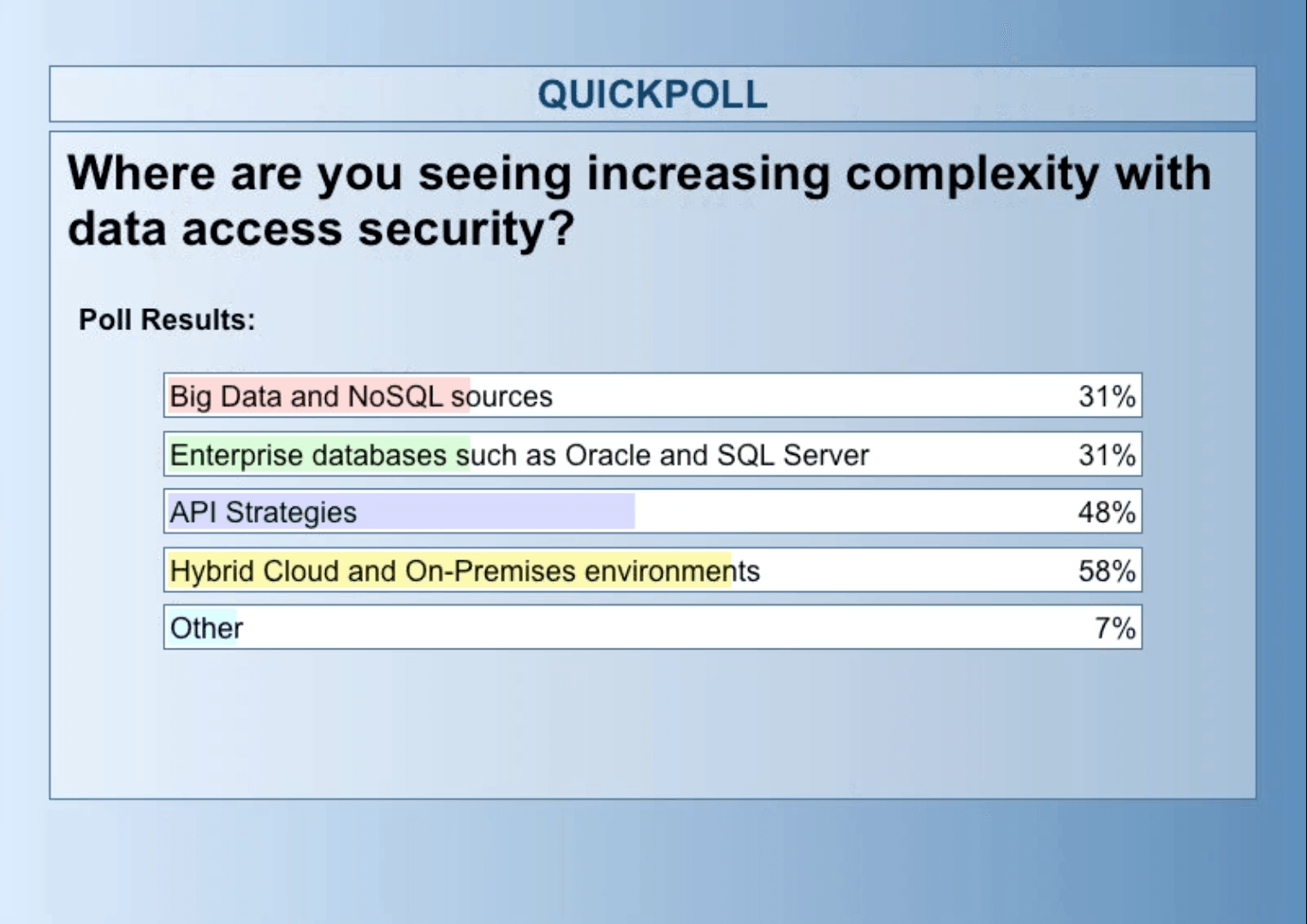
In short, the answer is that companies are seeing increased security complexity everywhere. Whether using traditional relational sources, Big Data or APIs, there is no simple, one size fits all solution to data access security needs. The technologies and implementations vary according to data stores, applications, API and use cases.
Latest Data Access Security Developments in the Industry
In this webinar, the speakers also spoke about technological advancements across different databases. While there is Knox, Ranger and Sentry for the Big Data world, the cloud data access security has seen OAuth, SSL / TLS, HTTPS, 2FA, MFA and other sophisticated technologies. On the relational side, the industry has moved from NTLM to Kerberos. There are a variety of encryption technologies including SHA, AES, Data Masking, Data Scrambling, WS-Security etc.
Even the databases themselves are increasingly supporting new technologies. For example, Oracle has Oracle Wallet and Oracle Internet Directory (LDAP). Access this webinar on-demand to learn about all these technologies and understand how to stay ahead of security risks.
Is it Possible to Test Enterprise Data Access Security?
While deciding on and implementing a security protocol may seem like the ultimate goal, the reality is that enterprise data access security extends far beyond the implementation.
Once you have your security plan in place, how will you test it for ongoing integrity? How will you continually update that security for new attacks, breeches, etc?
As an enterprise software vendor, Progress confronts those same challenges and we share our expertise in this webinar. We’ll tell you about our experience with VeraCode, PREfast, Fuzz testing, and other third party tools. We’ll also share details on the breadth of our security testing environments and how we handle new vulnerabilities with our Security Vulnerability Response policy. Join this webinar to learn how Progress DataDirect is delivering secure data access connectivity to its partners.
Learn More
Security is a complex topic, and that complexity continues to grow. To learn more about options and challenges implementing enterprise data security, including technologies such as Kerberos, SSL/TLS, Apache Knox, OAuth, Oracle Wallet, and more, watch our webinar today!

