5 Key Features to Look for in Secure Managed File Transfer Software

When evaluating a secure managed file transfer software, check out its security features, deployment options, logging and reporting capabilities, and more.
So, you’re in the market for a secure managed file transfer solution and want to invest in a product that will extend your defenses and help strengthen your security posture. With cyberthreats around every corner, you can’t afford to be lax when it comes to security.
As you start evaluating your options, there are key product features you should consider when making your decision. If a product is missing any of these, it’s probably not worth your time or money. After all, your company’s data and reputation are on the line.
Read on to discover the must-have capabilities to look for when purchasing a secure managed file transfer software. After narrowing down the options and choosing a solution, you can confidently transfer files and improve the security for your sensitive data.
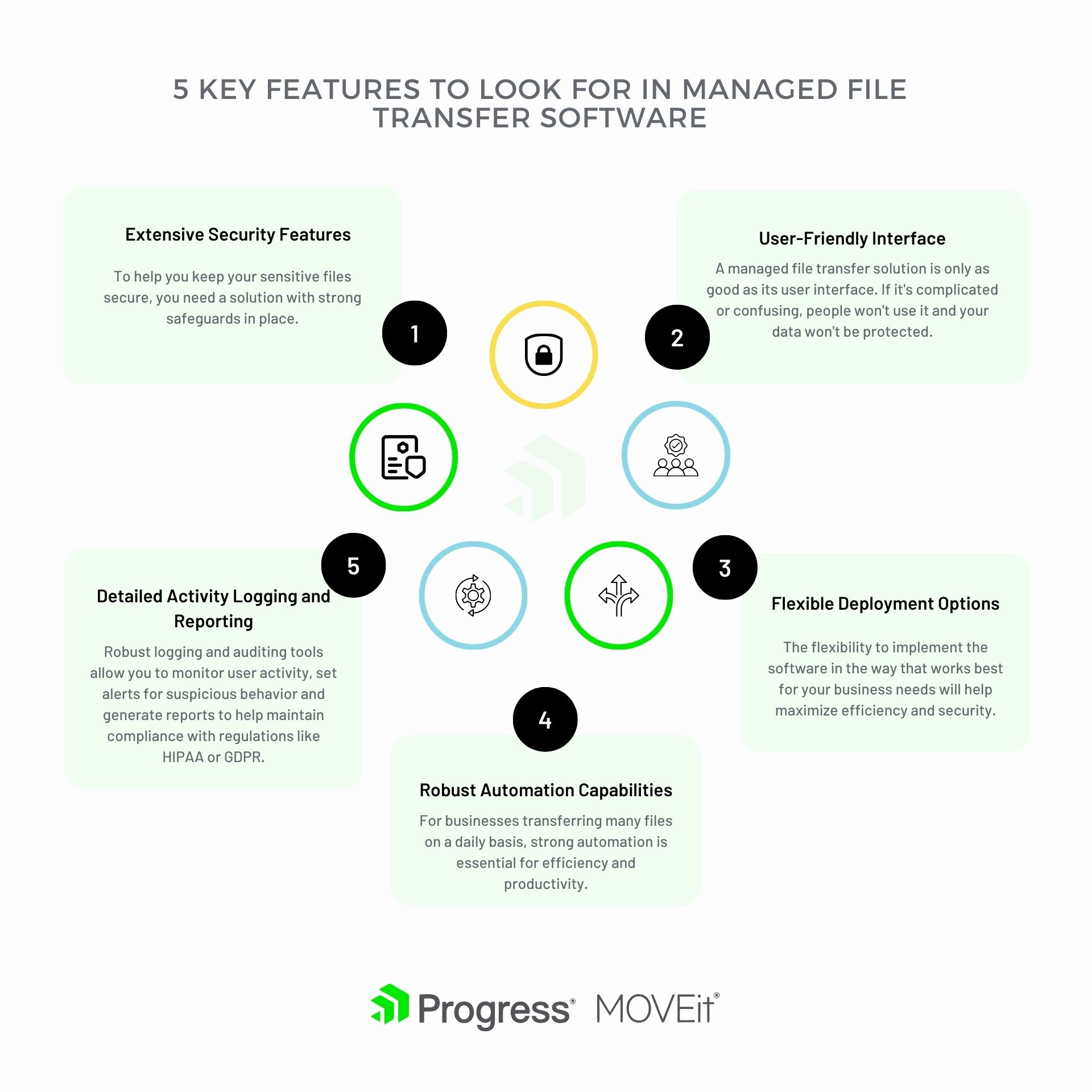
Feature #1 – Security Features
To keep your sensitive files secure, you need a solution with strong safeguards in place. Here are the top security-oriented features to look for in managed file transfer software:
Encryption
Encrypting your files during transfer and storage is critical. Look for 256-bit AES encryption to scramble your data and keep it private.
Granular Permissions
You need to be able to control access to files down to the user level. Most user-friendly software enables you to set view, edit, download and delete permissions for individual users or groups. This makes it so authorized individuals can interact with confidential data.
Audit Trails
Any time a file is accessed, uploaded, downloaded or deleted—a record should be kept. Audit logs allow you to see who did what and when, so you have visibility and accountability for file transactions.
Integrations with Existing Systems
For maximum security, your managed file transfer solution needs to integrate with your company’s authentication systems like Active Directory or Lightweight Directory Access Protocol (LDAP). This allows you to manage user access centrally and avoid creating separate login credentials.
Regular Updates
Software updates often contain security patches to help reduce vulnerabilities. Choose a solution that can be updated regularly to address existing and emerging threats, so you have the most recent protections in place.
Feature #2 – User-Friendly Interface
A secure managed file transfer solution is only as good as its user interface. If it’s complicated or confusing, people won’t use it and your data won’t be protected. Look for these key features in any software you’re evaluating:
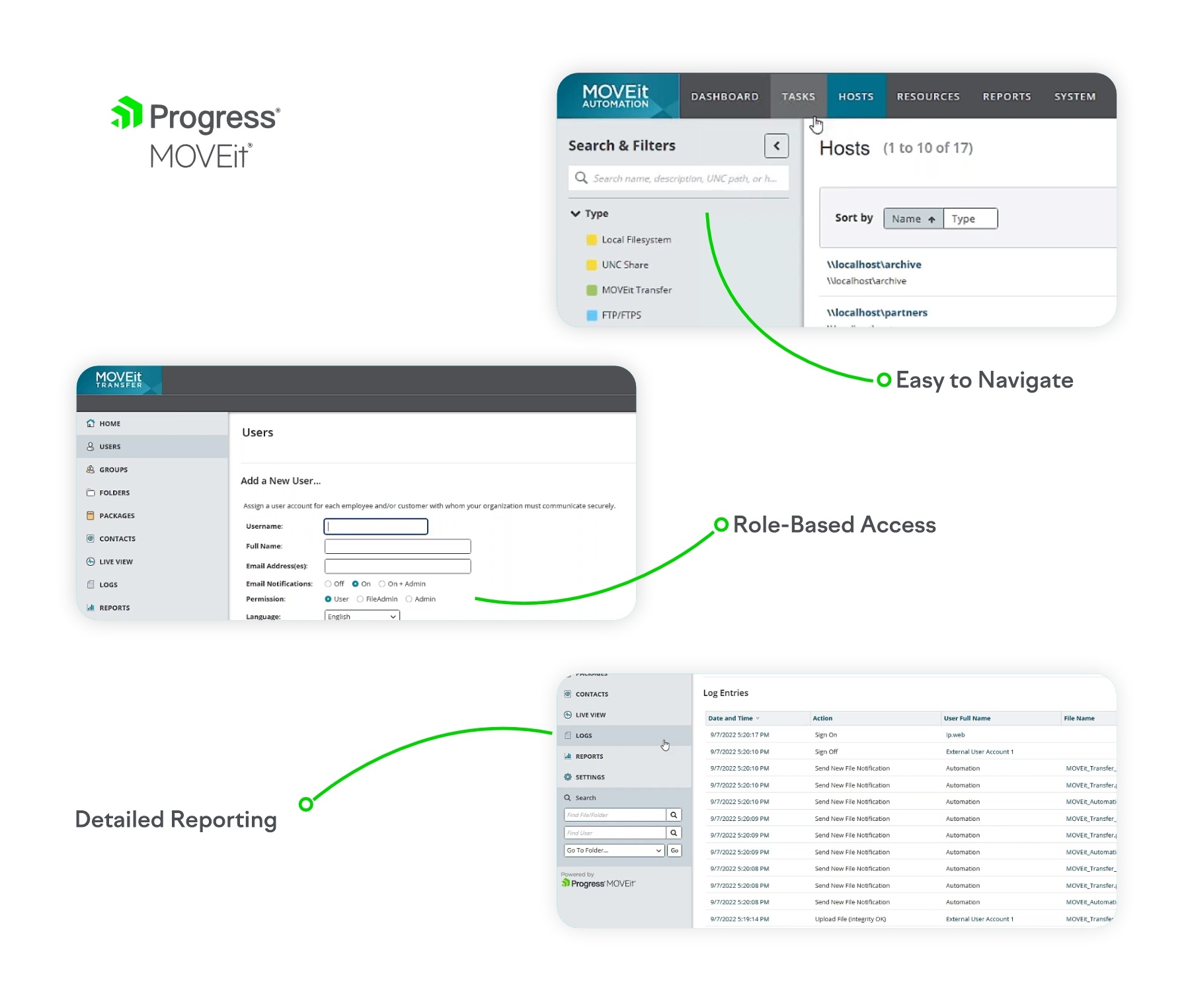
Easy to Navigate
The interface should be clean and intuitive. Anyone on your team should be able to log in and quickly find what they need, whether uploading, downloading or managing files. Things like drag-and-drop, smart folders that automatically organize files and global search make it simple to locate specific files.
Role-Based Access
Not everyone needs access to everything. Secure managed file transfer software enables you to more easily set up different user roles with customized levels of access. That way you can allow employees, clients and partners to only see what they’re supposed to.
Detailed Reporting
Thorough reporting tools let you see exactly how the system is being used. Look for options like audit trails that log who accessed or modified files, as well as summaries that show things like storage usage, number of uploads/downloads and bandwidth consumption over time. Detailed reports give you the insights you need to properly manage the system.
Customizable Workflows
Every organization has its own unique way of doing things. Flexible workflow automation lets you set up customized rules to help streamline your file transfer processes. For example, you can automatically move files to the right folders, rename them, trigger email alerts or convert files to different formats. Custom workflows save time and reduce errors.
24/7 Support
When you’re trusting software to handle sensitive data, you need to know help is there if you need it. Look for a provider that offers phone and email support 24 hours a day, seven days a week, 365 days a year. After all, data security never takes a holiday.
Feature #3 – Flexible Deployment Options
When choosing a secure managed file transfer solution, it is important to consider deployment options. The flexibility to implement the software in the way that works best for your business needs will provide increased efficiency and security.
Cloud-Based
A cloud-based deployment means the software is hosted by the vendor in the cloud. All you need is an internet connection and login credentials to access the platform. This is an easy-to-use, low-maintenance option since the vendor handles all the technical requirements like servers, storage and updates. However, some companies prefer to keep sensitive data on-premises.
On-Premises
An on-premises deployment means installing the software on your own servers within your organization’s infrastructure. This method provides control and ownership of your data, platform and security. However, your IT team will need to handle the installation, maintenance and updates, which requires more time and resources. This may be a good choice if you have strict security and compliance requirements.
Hybrid
A hybrid approach combines the best of both worlds—part cloud and part on-premises. Some components reside in the cloud while other parts remain in your own data center. Sensitive files and large transfers can be kept internally, while other tasks like reporting, analytics or workflow automation utilize the cloud. The hybrid model provides more flexibility and control but is often the most complex to set up and manage.
The right deployment method for your needs depends on your security requirements, compliance standards, IT resources and how much you want to rely on a vendor versus handling technology matters in-house. Reputable secure managed file transfer solutions will provide options to suit your unique situation. Choosing a solution with flexible and customizable deployment is key to maximizing both security and ease of use.
Feature #4 – Robust Automation Capabilities
Once you’ve narrowed down secure managed file transfer software options based on security, compliance and easy-to-use features, look closely at the automation capabilities. For businesses transferring many files daily, a strong automation tool is essential for efficiency and productivity.
Scheduling
With robust scheduling, you can automate file transfers to run at set times. This eliminates the need for manual uploads and allows files to be transferred on schedule. Look for software that allows you to set up recurring transfers daily, weekly, monthly or annually and specify the precise time of day the transfer should run.
Event-Based Triggers
Event-based triggers are ideal for time-sensitive file transfers that need to happen immediately. These triggers can automatically start a file transfer when a file is added to a folder, a database record is updated or an API call is made. A majority of automation software will provide pre-built triggers for common events as well as the ability to create custom triggers tailored to your business’s needs.
File Processing
Once files have been transferred, additional automated file processing helps streamline workflows. Look for options like automatically deleting source files after transfer, moving or renaming files, converting files to different formats or calling scripts and APIs. With file processing, you can automatically organize, optimize and backup files as soon as they’re transferred.
Monitoring and Alerts
Even with automation, it’s important to monitor file transfers and be alerted immediately if there are any issues. Robust software will monitor most of your organization’s automated file transfers and send email or SMS alerts if a transfer fails or is delayed. With proactive monitoring, you can catch any problems early and avoid disruption to your file transfer workflows.
Feature #5 – Detailed Activity Logging and Reporting
When evaluating secure managed file transfer software, detailed activity logging and reporting is crucial. As a business, you need to know who is accessing what data and when. Robust logging and auditing tools allow you to monitor user activity, set alerts for suspicious behavior and generate reports to check compliance with regulations like HIPAA or GDPR.
Activity Logging
Look for software that logs details like:
- User login/logout times
- Files uploaded, downloaded or deleted
- Changes made to user accounts or security settings
- Failed login attempts
The logs should capture the user’s name, IP address, timestamp and details of the activity. Storing log data for at least 90 to 365 days is ideal for auditing purposes. Some software also allows you to set alerts, like notifications when a user logs in outside of normal business hours.
Reporting
Reporting tools should provide an at-a-glance view of file transfer activity across your organization. Look for options to filter reports by:
- Date range
- User or group
- IP address
- File type, name or size
- Success/failure status
The reports should be exportable to formats like PDF, CSV or XML for sharing with auditors or compliance officers. Some software includes pre-built reports for standards like HIPAA, SOX or GDPR to simplify and maintain compliance.
Dashboards
An intuitive dashboard gives you an overview of file transfer activity from one central place. Look for options to customize the dashboard with reports, statistics, alerts and more. Things like visual graphs of upload/download volumes, user logins over time or top file types transferred can help identifying trends and areas that may need attention.
Concluding Thoughts
Choosing a secure managed file transfer software solution with strong encryption, user authentication, detailed audit trails, simplified file tracking and an intuitive interface will give you peace of mind when transferring your files. Implementing the right solution for you and your team’s needs means less time focusing on potential vulnerabilities and more time focusing on what really matters—growing your business.
Progress MOVEit better enables your organization to meet strict cybersecurity compliance standards such as PCI-DSS, HIPAA, GDPR, SOC2 and more. It comes with a 30-day free trial, so try MOVEit today.

