SAML Authentication for your Rollbase Private Cloud Accounts

Using SAML, an online Service Provider can contact a separate online Identity Provider to authenticate users who are trying to access secure content. Learn how to do this with Rollbase and Okta as an example.
Authentication is playing a vital role in cloud based applications. Nowadays users are not interested in remembering each password for each cloud application, and nobody wants to store their password in the application platform. To overcome this, any application which implemented support for SAML-based authentication can configure with any SAML based IDP (Identity Provider).
There are many Cloud IDPs (Okta, PingOne, Salesforce, One Login, etc.) and hosted IDPs (Open AM, Open Select, Shibboleth, etc.).
Applications are authenticating with the above IDPs using SAML. SAML authentication involves following three entities:
- Service Provider
- Client
- Identity Provider
Security Assertion Markup Language (SAML) is an XML standard that allows secure web domains to exchange user authentication and authorization data. Using SAML, an online Service Provider can contact a separate online Identity Provider to authenticate users who are trying to access secure content. There are three major components for SAML authentication.
(a) Client (Users)
This is the user who can login to any cloud application.
(b) Identity Provider (IDP)
Identity Provider is responsible for:
- Providing identifiers for users looking to interact with a system
- Asserting to such a system that such an identifier presented by a user is known to the provider
- Possibly providing other information about the user that is known to the provider
- Acting as a trusted provider that lets you use single sign-on to access other websites
(c) Service Provider (SP)
In the use case addressed by SAML, the principal requests a service from the Service Provider. The Service Provider requests and obtains an identity assertion from the Identity Provider. On the basis of this assertion, the Service Provider can make an access control decision—in other words it can decide whether to perform some service for the connected principal.
To configure SAML authentication we need to set up things in our Identity Provider and Service Providers:
- Should have SP metadata (i.e., our application data to register in the Identity Provider)
- Should register SP in IDP (information about registration can be found in the IDP's documentation)
- Need to get IDP metadata to register IDP in our application (SP)
- In our application we should register IDP with IDP metadata
In Our case Rollbase acts as a Service Provider and PingID, Okta, Onelogin, Salesforce and OpenAm are the Identity Providers we certified.
As the data transformation between SP and IDP must be encrypted, we'll follow two step Asymmetric encryption. To achieve the Asymmetric encryption we need to have a public certificate which will be shared with IDPs and the respective keystore, which consists of private key.
Registering the Service Provider in the Identity Provider
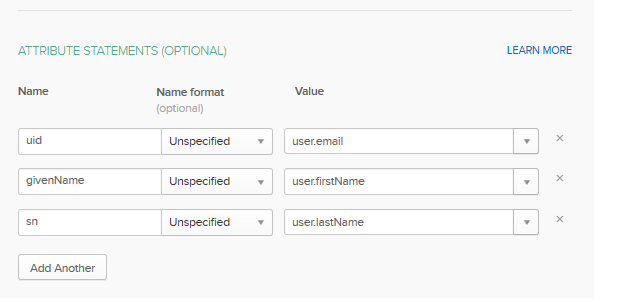
Registration of the SP in any IDP requires the ACS (Assertion Consumers) URL of the SP (Ex: http://yourhostname/router/login/loginSaml), the Public key and the Entity ID of the SP (Ex: http://yourhostname). And make sure users have given enough permission to access the given application. You'll need to add the attributes in the IDP with user fields to consume by the SP (Rollbase). Example attributes you may need to add include: givenName ,sn, uid and city.
After successful registration of the SP we need to download the IDP metadata file, which is important to configure at SP side.
Registering the Identity Provider in the Service Provider
Now we are allowing Rollbase users to setup authentication at two levels:
Global Level
Setting Global level SAML authentication will not allow any customers to change their authentication mechanism. For this we need to register the IDP in shared.properties with following properties.
AuthOverrideAtCustomer=false
This property will disable from setting authentication at tenant level:
DefaultAuthType=SAML
This property will explain type of authentication mechanism type:
IdPId=https://IDPURL.com/ABC/qazwsx
This property will identify the IDP. The value of this is the value of EntityID in IDP metadatfile:
SPId=http://yourhostname
This property value is the value given at the time of registering the SP in the IDP:
IdPMetadataFile= IDPMETADATAFILE.xml
This property value is the name of the IDP metadata file:
AttributeMap=firstName=givenName|lastName=sn|loginName=uid|city=city
Left side values of attribute map are the field that are related to Rollbase, which will be associated with right side values which will come from the IDP:
SPKeyStoreFile=encryption.keystore ot encryption.jks
The value for this is the name of keystore we have and with which public key we registered in IDP:
SPKeyStorePassword=keystorepassword
Value given while generating the keystore:
SPKeyStoreAlias=aliasname
Value given while generating the keystore:
AssertionConsumerIndex=2
By default, the value is 2 as in the IDP metadatfile Single signon HTTP redirect index.
And also we need to place the keystore file in our rollbase config folder (ROLLBASE_HOME/config).
Restart the Rollbase instance.
Tenant Level
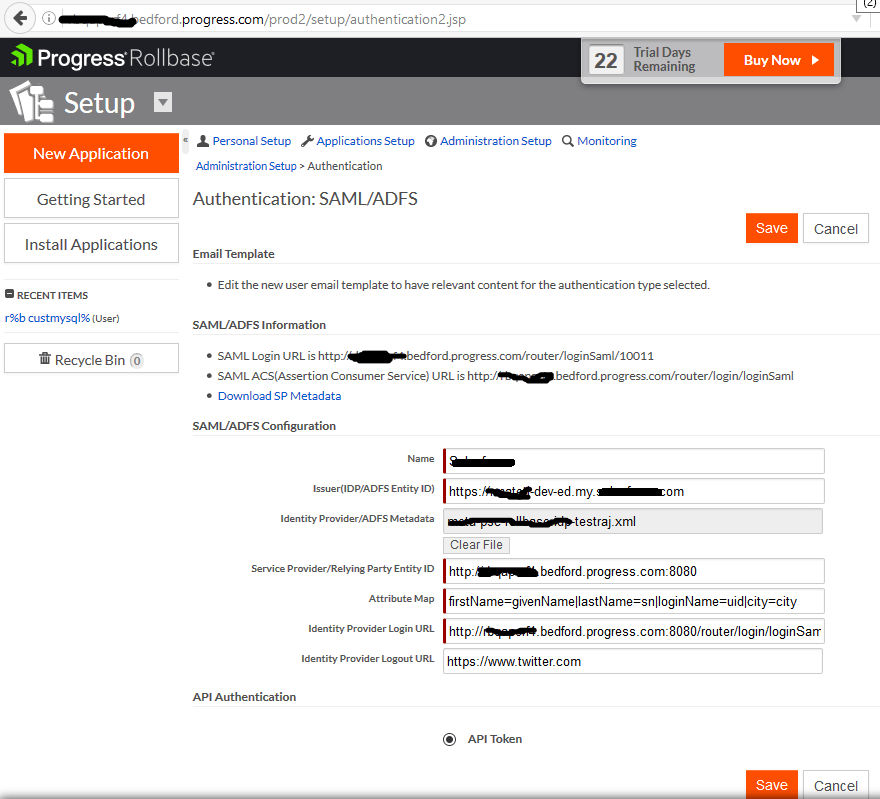
Login as tenant administrator, navigate to setup home from setup application or setup home in the hamburger menu. Click on Authentication, click on the SAML radio button and click on next.
Enter a name for the Name field.
Enter the Issuer (IDP Entity ID) entityID value in IDP metadata file (Ex: https://IDPURL.com/ABC/qazwsx).
Upload the IDP metadata file downloaded from Okta.
Enter the Service Provider Entity ID value given while registering in IDP (Ex: http://youhostname).
Enter the Attribute Map value as firstName=givenName|lastName=sn|loginName=uid|city=city
Enter the value for the Identity Provider login URL from your SAML ACS URL value in the SAML information section on the same page.
Enter a value for Identity Provider Logout URL (Ex: www.google.com)
Note the Login URL from SAML information section.
Click on Save.
Logout from tenant.
Open the browser with the above Login URL noted
Refer here for more details.
Registering Rollbase in Okta
The following example shows setting up the Rollbase authentication with the Okta IDP. Details of configuring sample IdPs with Rollbase can be found here.
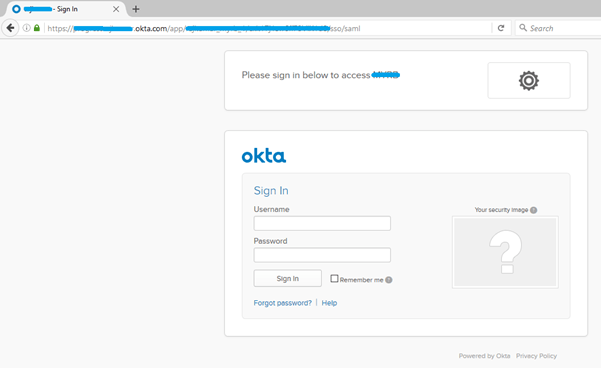
Login to Okta https://www.okta.com/platform-signup/
Open the welcome email which came to your registered email address, and click on the Sign-in here link.
Login with details got from welcome email.
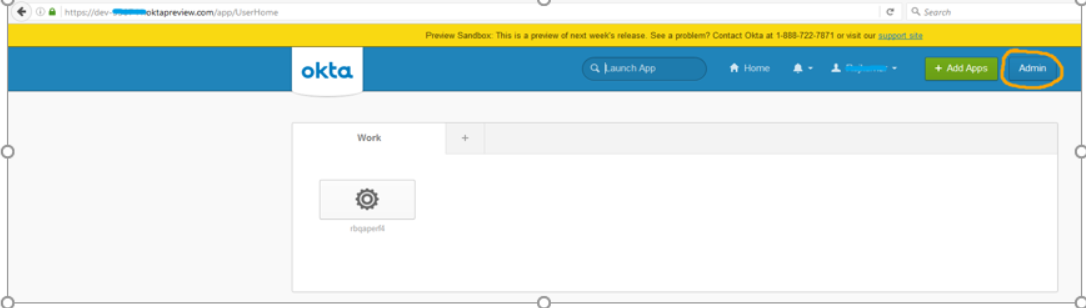
Click on the Admin button.
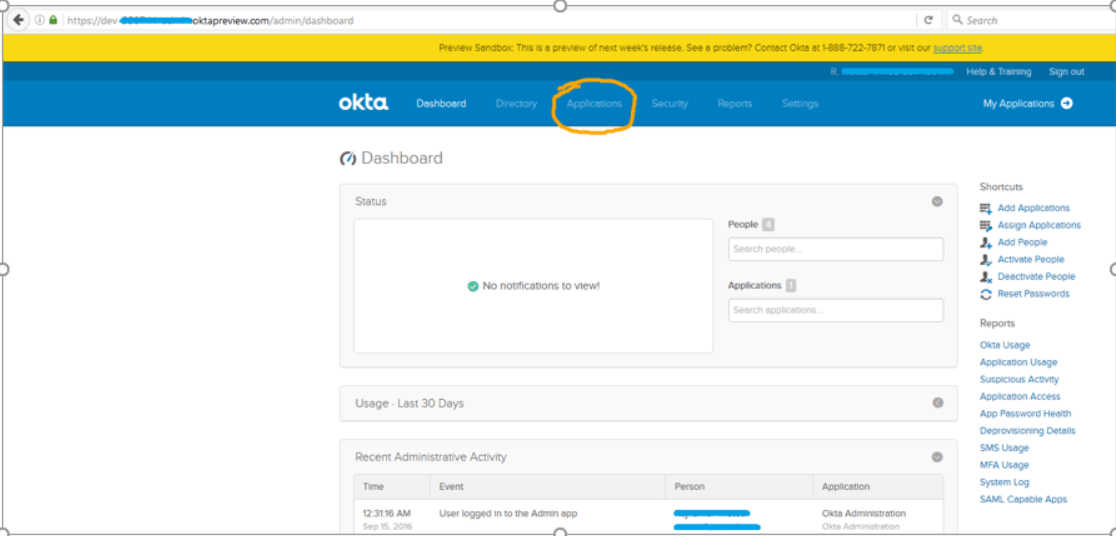
Click on the Applications menu in the header.
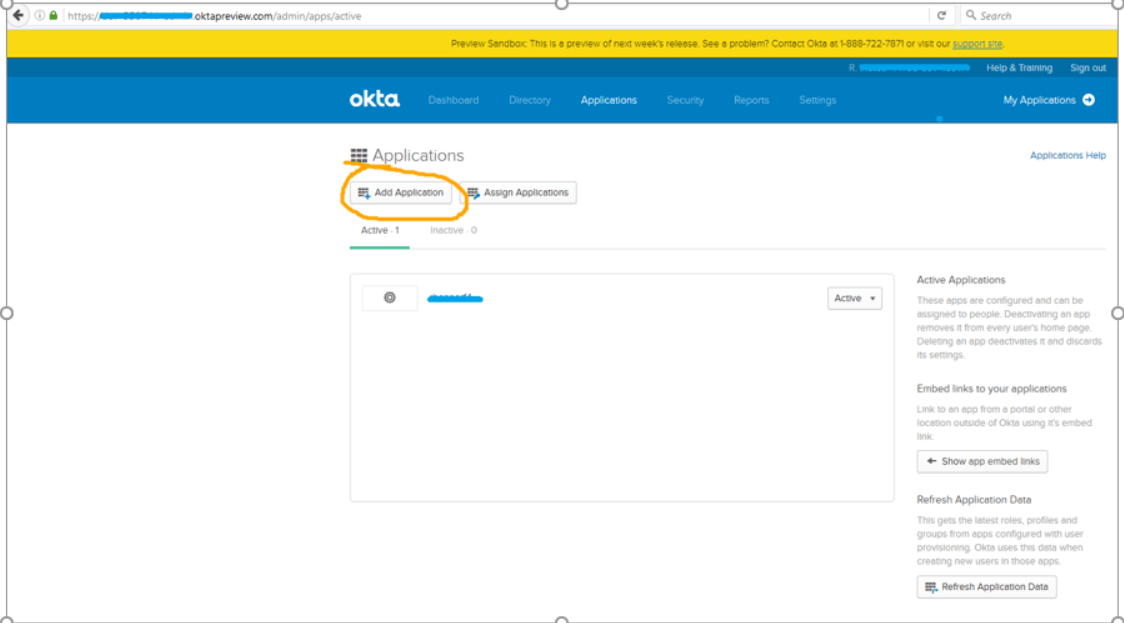
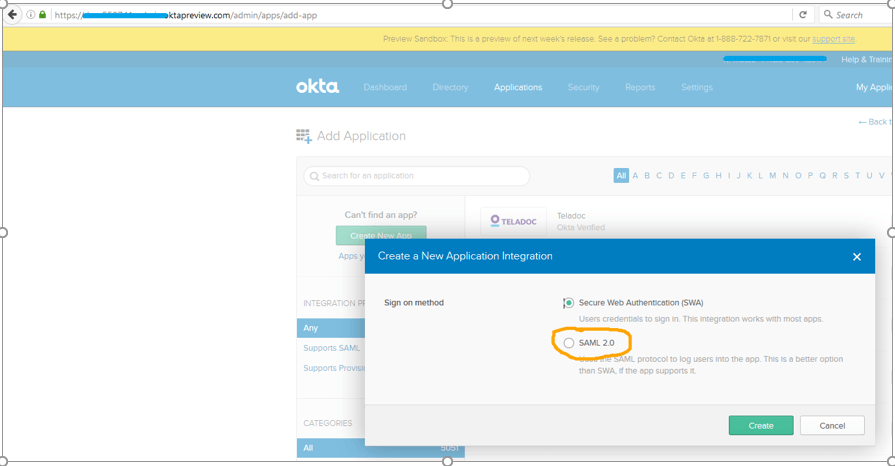
Click on the Add Application button.
Click on the Create New App button.
Select the SAML 2.0 radio button and click on the Create button.
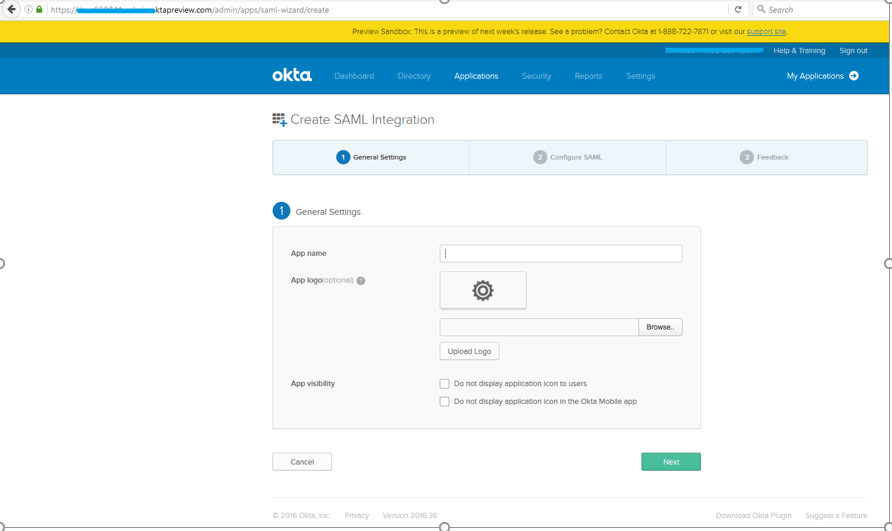
Provide the App name and click on Next.
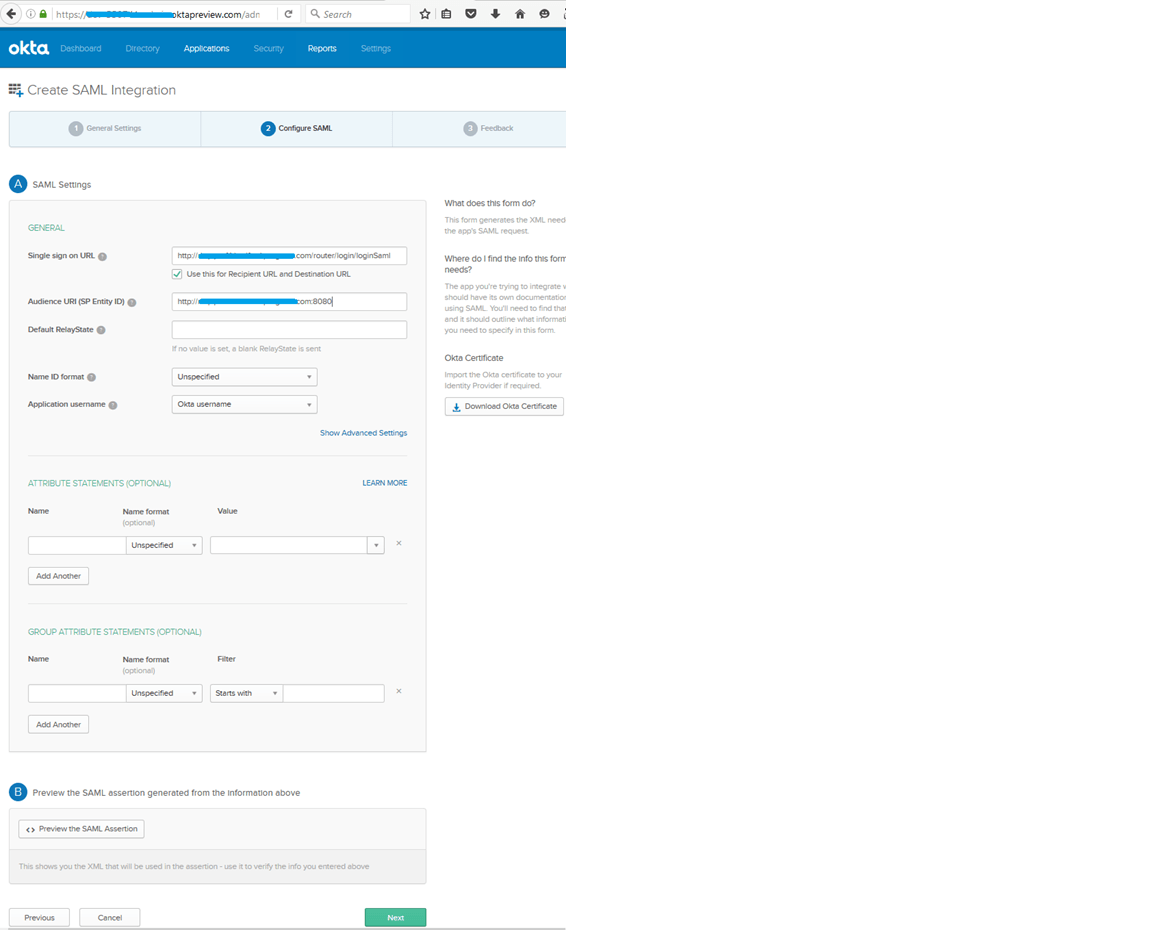
Provide Single Sign on URL and Audience URI, and then click on the Show Advanced Settings button.
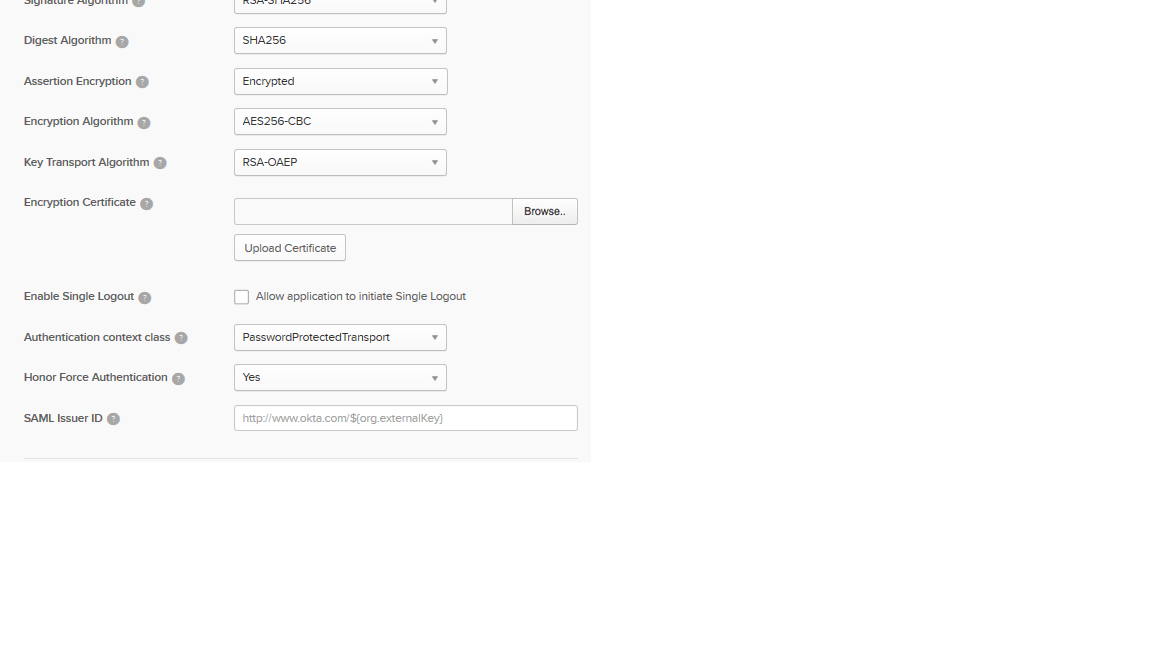
Change the Assertion Encryption value to: Encrypted.
Upload the certificate from Browse and click on the Upload Certificate button. Make sure the following appears on your screen:
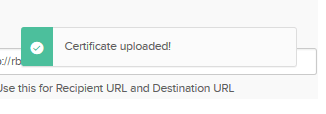
Add Attributes, which are defined in the Attribute map, with Okta user fields as shown in the above screen. Then click on the Next button.
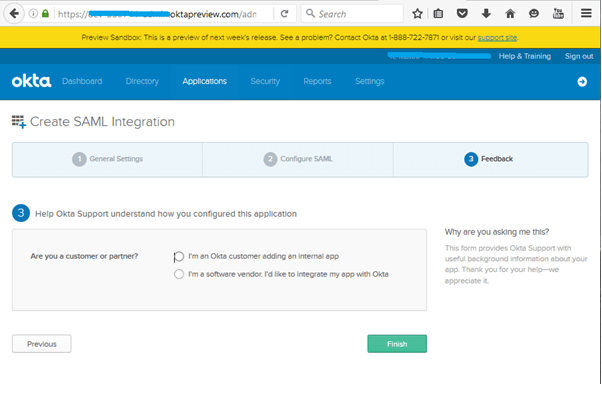
Provide feedback as you wish, which will not affect anything, and click on Finish.
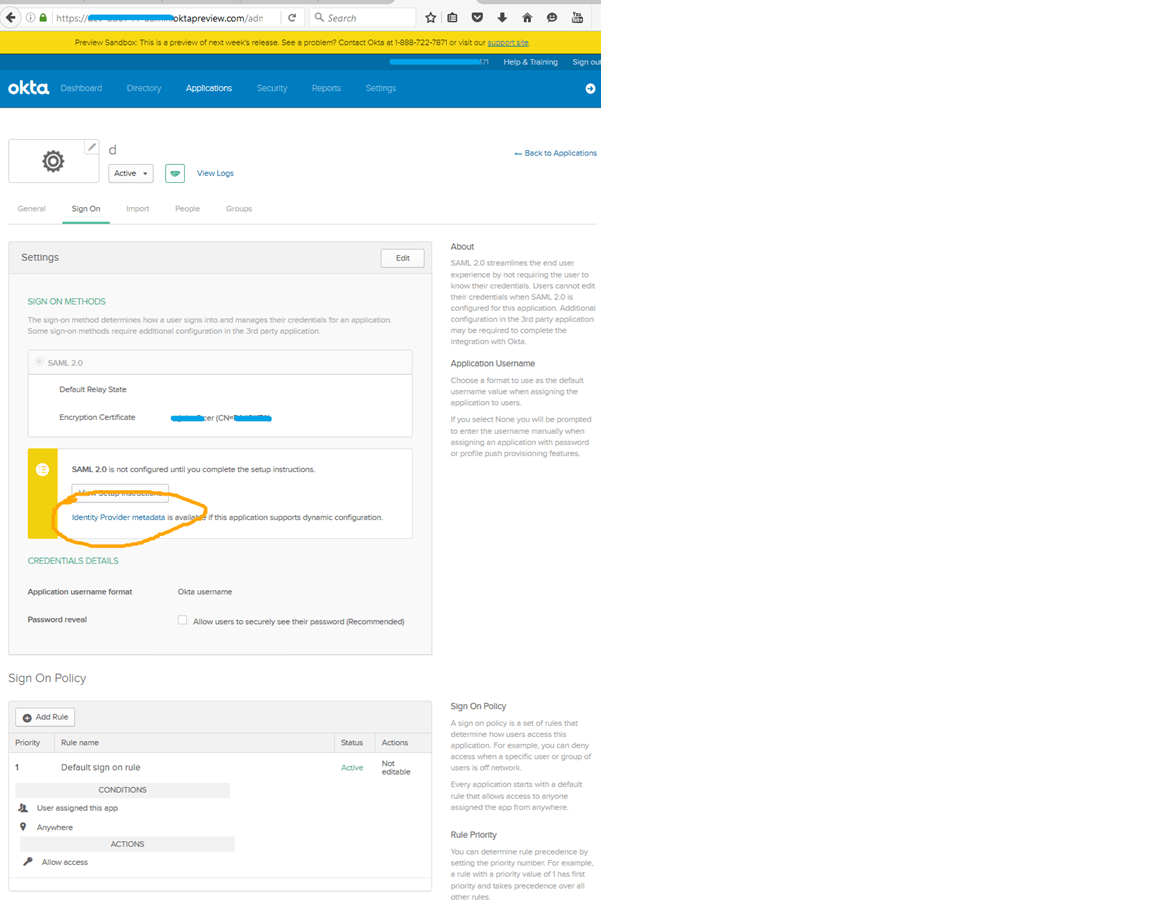
Click on the Identity Provider metadata link. It will download and save the file with format to .xml. Later we will use this file to register this IdP in the service provider.
Registering Okta in Rollbase
Global Level
The following shared.properties need to be added along with placing the keystore file in rollbase config folder (ROLLBASE_HOME/config):
AuthOverrideAtCustomer=false
DefaultAuthType=SAML
IdPId=https://IDPURL.com/ABC/qazwsx
SPId=http://yourhostname
IdPMetadataFile=youridpmetadatafilename.xml
AttributeMap=firstName=givenName|lastName=sn|loginName=uid|city=city
SPKeyStoreFile=yourkeystirname.keystore
SPKeyStorePassword=yourkeystorepassword
SPKeyStoreAlias=yourkeystorealiasname
AssertionConsumerIndex=2
Tenant Level
Login as tenant administrator, navigate to setup home from setup application or setup home in the hamburger menu. Click on Authentication, Click on the SAML radio button and click on next.
Enter a name for the Name field.
Enter the Issuer (IDP Entity ID) EntityID value in the IDP metadata file (Ex: https://IDPURL.com/ABC/qazwsx).
Upload the IDP metadata file downloaded from Okta.
Enter the Service Provider Entity ID value given while registering in the IDP (Ex: http://youhostname).
Enter the Attribute Map value as firstName=givenName|lastName=sn|loginName=uid|city=city
Enter the value for the Identity Provider login URL from your SAML ACS URL value in the SAML information section on the same page.
Enter a value for the Identity Provider Logout URL (Ex: www.google.com).
Note the Login URL from the SAML Login URL from the SAML information section.
Click on Save.
Accessing Rollbase with Okta IDP
Global Level
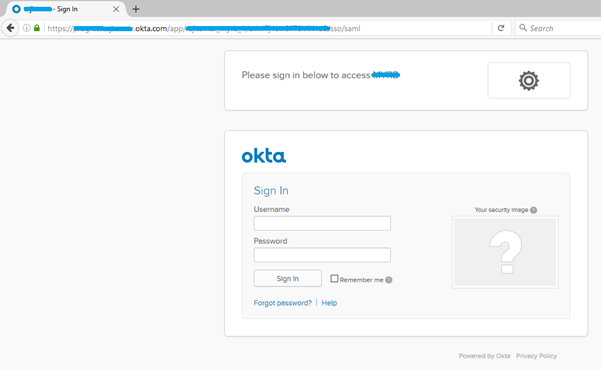
Any user who visits the http://yourhostname/router/login/loginPrivate.jsp, or any bookmarked URL, will have to navigate to the Okta login page.
Enter the Okta user name and password.
User will be navigated to Rollbase.
Tenant Level
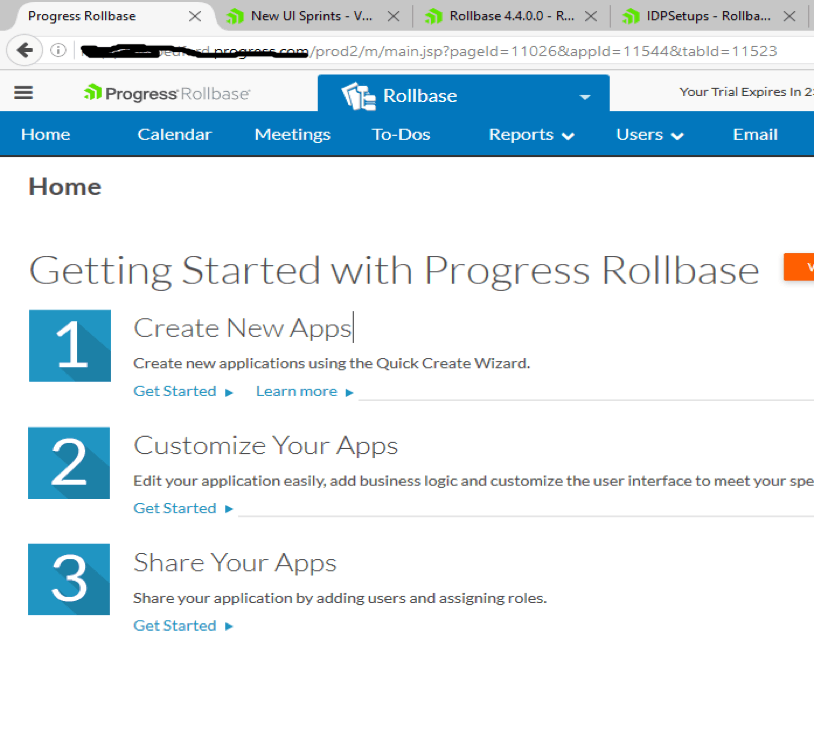
Login as tenant administrator, navigate to setup home from setup application or setup home in hamburger menu. Click on Authentication, Click on the SAML radio button and click on next. Provide the value as shown in following image:
Click on Save.
Logout.
Head to the SAML Login URL which is in the above image. You will get redirected to the Okta login page.
Enter the Okta user name and password.
User will be navigated to Rollbase.
Secure SAML Authentication for Your Rollbase Apps
With the increasing importance of authentication in cloud-based applications, it's important to give your users the options they want. With Rollbase you can easily give your customers what they're looking for with SAML-based authentication. Let us know how this is working for you in the comments below.