An Introduction to Exploit Kits


In early June, the news broke that the Angler exploit kit was no longer the method of choice for malware delivery, especially ransomware. According to SC Magazine, attackers have now switched to the Neutrino exploit kit, perhaps in an effort to avoid detection.
Exploit kits have become one of the preferred methods for attacking users in both corporate and home environments. Understanding what exploit kits are and what they do is critical to your ability to keep your network safe. In this article, we'll cover the basics of how these kits work and what you can do to protect your users.
Why Do Hackers Use Exploit Kits?
Cyber criminals that want to cause havoc on end-user computer systems basically have two methods of attack: direct or indirect.
The direct approach involves sending malware to potential victims via email or an instant messaging channel. But, from the attacker's point of view, this has some downsides:
- Malware can be intercepted or filtered in transit (for example, when malware is attached to an email).
- Once it has been intercepted and the different a/v signatures have been updated, the attacker has to refactor the malware.
- It is fairly obvious to the user that something fishy is going on. They have to click the link included in the email message or open the attached malware. The malware will rarely execute on its own.
Attackers want something sneakier, something that does not set off alarms for end-users: an indirect approach.
In addition to reading emails, users spend a lot of time on the internet surfing websites. And, from an attacker's perspective, there's a lot of gain by introducing malware via a channel that's already being heavily used by users: websites.
How Does an Exploit Kit Work?
An exploit kit is a method for delivering malware to an unsuspecting user while that user is surfing the web, without requiring any interaction from that user. It uses vulnerabilities in browsers or browser-related software (plugins) to infect a device.
Today, most exploit kits are available as malware-as-a-service, according to ZDNet. This means that, instead of buying an exploit kit and doing all the hard work, an attacker can simply "rent" the latest kit with the newest exploits and get started.
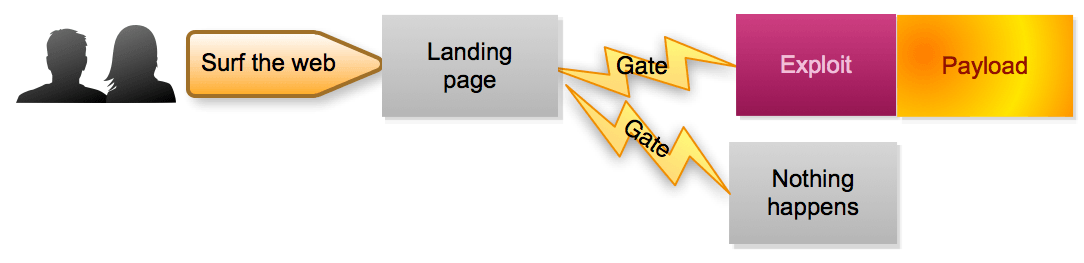
The Landing Page
The first step in an exploit kit is a landing page. The landing page is a piece of web code that profiles the user or more precisely, the user's web browser, together with all the available plugins. The code will check whether there are any vulnerabilities that can potentially be exploited. It basically inventories the technology that you use to browse the internet and checks to see whether anything can be abused.
This is one of the reasons why it's so important to only use fully patched systems to get online. If your systems are fully patched it will be much harder for attackers to get through.
Harder, but not impossible. Zero-day vulnerabilities are flaws in software or hardware that have not yet been patched. Attackers can exploit these vulnerabilities to release their malware. However, you will rarely see attackers using zero-day vulnerabilities to mount large-scale, bulk attacks. Instead, zero-day vulnerabilities are usually used in targeted attacks.
The Gate
This leads us to the second component of an exploit kit: the gate. The gate is code that evaluates whether the visiting user is within the scope of the attacker's campaign or not. Being "in scope" can mean a few different things:
- The user is using an exploitable platform. (If an attacker is targeting Windows users, there's no need to waste resources on Linux users.)
- It is a "real" system, not a sandbox being used by a researcher.
- The user is coming from the geographical area that the attacker wants to target. (If the campaign is targeting users in the Middle East, there's no point in wasting resources on users in Europe.)
The gate can be even more sophisticated. For example, it can be made to only allow users through that have a very specific language set or browser plugin installed.
Launching the Attack
Obviously, users are not going to visit a landing page or a gate on their own. So, how do they end up there? The code (or more precisely an inclusion or redirect to it) is hosted on a legitimate website that has been compromised by attackers. When an unsuspecting user visits the page (and downloads the web assets), he also receives the necessary code to kick-start the exploit kit.
Note that sometimes it's not the legitimate website that has been compromised. Instead, attackers may use compromised third-party content providers (such as advertisement providers) whose content is being hosted by the legitimate website.
Now, if you combine a sophisticated gate that only lets specific users through and you only redirect users visiting well-chosen (compromised) websites, you, as an attacker, can launch a very targeted, sneaky attack campaign. But what else happens after the user ends up on the landing page? Basically, the profiling has been done and the kit knows exactly what exploit can be thrown at the browser, or in most cases, the browser plugins (Flash, Silverlight and Java). The exploit will abuse the vulnerable application and instruct it to run a piece of malware, called the "payload." Often this payload is a tiny piece of software that will do just one thing: download the "real" malware that will cause havoc.
This malware can be a keylogger, DDoS client or ransomware. It is up to the imagination (and capabilities) of the attacker to decide what they want to do after a successful infection.
How Do I Protect My Users Against Exploit Kits?
As explained earlier, an exploit kit needs a point of entry — a vulnerability — to be successful. The best way to protect your users is to remove this entry point. Patch and update all the software that is in use. True, this will not address zero-day vulnerabilities, but the majority of attacks exploit patched vulnerabilities anyway.
You can also prevent your users from visiting any known malicious or compromised websites (either directly or via a redirect). Make sure your users surf the web via a central proxy that uses proper filtering. Do not forget to update the filter list continuously using information from threat feeds.
Last, but not least, educate your users. Instruct them not to click on suspicious links in emails or when surfing the web.
