Authentication
Overview
Sitefinity CMS uses claims authentication, implemented on top of IdentityServer3, certified by OpenID Foundation. It allows implementing single sign-on and access control for modern web applications and APIs. It uses OAuth2 and OpenID Connect protocols. This integration allows easy connection with clients such as mobile, web, SPAs ,and desktop applications. It is also extensible and allows integration in new and existing architectures.
The authentication is designed and implemented as separate Microsoft OWIN / Katana component. It uses standard Microsoft.Owin.Security libraries and standard namespace System.Security. Additionally, there are some extensions to support external provider logins, such as Facebook or GitHub.
Advantages
Authentication model in Sitefinity CMS has the following advantages:
- Improved security
Users do not have to deploy same passwords and accounts across multiple websites. Using OpenID Connect, passwords are never shared with any websites.
- Standardized authentication, based on OpenID Connect with JWT, certified IdentityServer3.
- Out-of-the-box support for logging in with your Windows, Facebook, Google, Microsoft, Twitter, LinkedIn, or GitHub account.
- Better extensibility.
Easy extension for any other OpenId Connect external providers. You can use some of already available OWIN implementations and plug it in Sitefinity CMS.
- Login with email
Easier to remember, simplifying the management of collisions, better for email verification and password recovery.
- API improvements
Using standard Principal class, standard System.Security, and cleanups
- Ability to configure your own STS certificate
Authentication flow
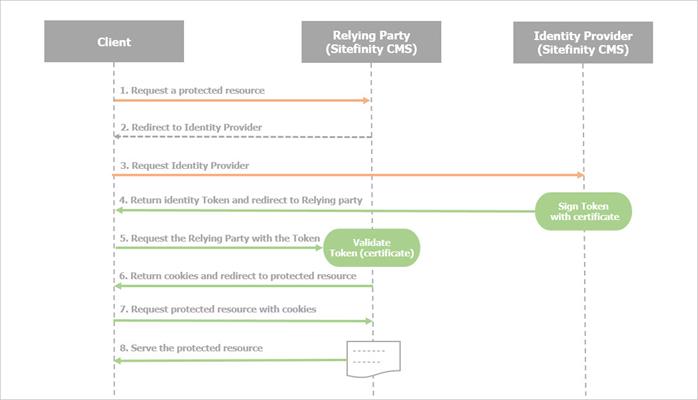
Sitefinity CMS can serve both as Relying Party (RP) and Identity Provider (IP). Usually, these can be one web application on the same host, but with different URLs. However, in a Single-Sign-On (SSO) scenario, these can be on different servers (applications). In both cases the communication between IP and RP is via HTTP and goes trough the client.
Authentication flow diagram
Configure certificates for your site
To ensure security, you must configure the following two types of certificates for Sitefinity CMS:
- SSL/TLS certificate for the site
This certificate ensures the identity of the URL that is requested by the client (browser). It is used in all the steps from the above diagram.
NOTE: Although Sitefinity works successfully on HTTP and HTTPS, we recommend to use SSL/TLS certificate for your site.
- Identity server signing certificate
This certificate is used to verify the issuer of the authentication token – it is used by Sitefinity CMS Identity provider to sign the identity token (Step 4 in the diagram). It is also used by Sitefinity CMS Relying party to ensure that the authentication token has been issued by the correct Identity provider (Steps 6 in the diagram).
You must configure this certificate, by navigating to Administration » Settings » Advanced » Authentication » SecurityTokenService » IdentityServer » SigningCertificate.
NOTE: The certificate must have a private key and the application pool user that runs Sitefinity CMS identity provider must have rights to access it to use it for signing.